Configuration OIDC (OpenID Connect)
OpenID Connect (OIDC) is an authentication protocol that allows users to verify their identity and access web applications using a third-party trusted provider (IDP).
OpenID is based on the OAuth 2.0 specifications (IETF RFC 6749 and 6750). It simplifies the way users' identities are verified based on the authentication performed by an authorization server and retrieves user profile information in an interoperable and RESTful way.
OpenID Connect enables users to authenticate and access web applications using an Identity Provider (IDP) that is trusted by both the user and the website or application.
Hideez Enterprise Server acts as an IDP, which prevents the loss of credentials, and their leakage during storage or installation, and helps with password management.
The OpenID Connect protocol for Hideez Enterprise Server works as follows in general terms User initiates an authentication request:
The HES user initiates an authentication request to access a secure resource on a website. The request is sent to the OIDC client, which is the application that requires user authentication.
The OIDC client sends an authorization request to the IDP (HES): This request contains the client's identity, scope, and the redirect URL where the user will be sent after the authentication process is complete.
IDP (HES) authenticates the user: this includes Passwordless authentication or Two-factor authentication (MFA). Once the user is authenticated, the IDP generates an access token and sends it back to the OIDC client.
The OIDC client verifies the access token received from the IDP. This includes checking the token signature, expiration date, validity period, etc. This is to ensure that the token is valid and has not been tampered with.
The OIDC client requests information about the user from the IDP (HES): If the access token is valid, the OIDC client sends the IDP a request for user information. This request includes the access token as well as a request for specific information about the user, such as their name, email address, and other attributes.
The IDP (HES) sends the user information to the OIDC client. This information is typically in the form of a JSON Web Token (JWT) that contains the user's identity information as well as any additional assertions requested by the OIDC client.
Finally, the OIDC client can authenticate the user based on the information received from the IDP. If the user is successfully authenticated, he or she is granted access to the secure web application resource.
Configuring OpenID Connect on HES
Open Settings → Parameters → OIDC section
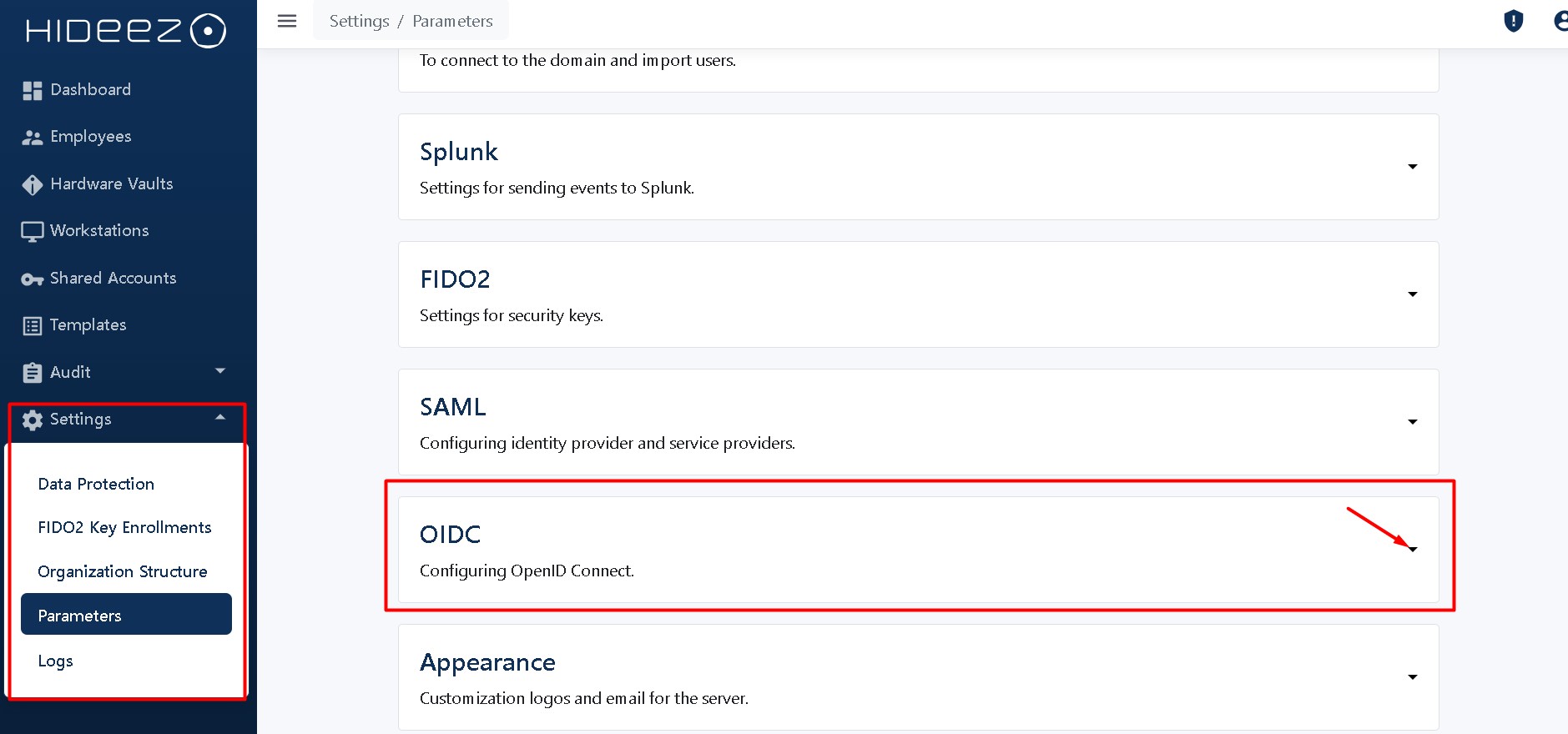
Enable OIDC
To protect the tokens, OIDC by 2 types of credentials:
Signing credentials are used to protect against tampering.
Encryption credentials are used to ensure the content of tokens cannot be read by malicious parties.
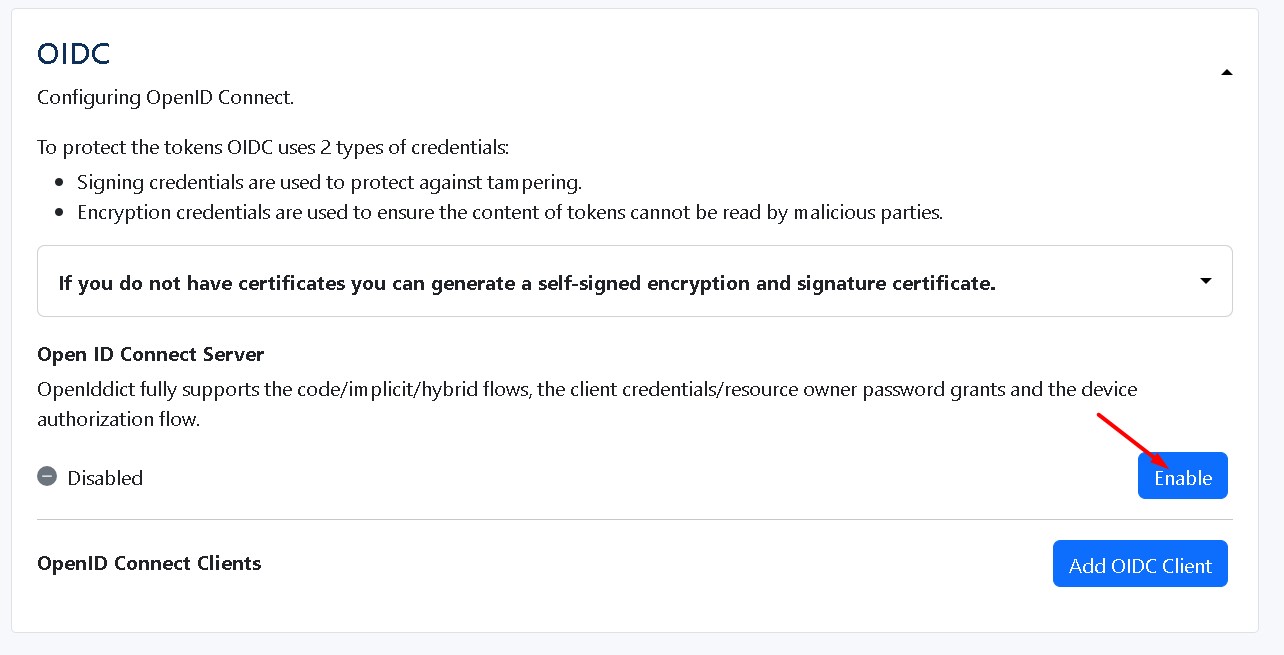
If you do not have certificates you can generate a self-signed encryption and signature certificate:
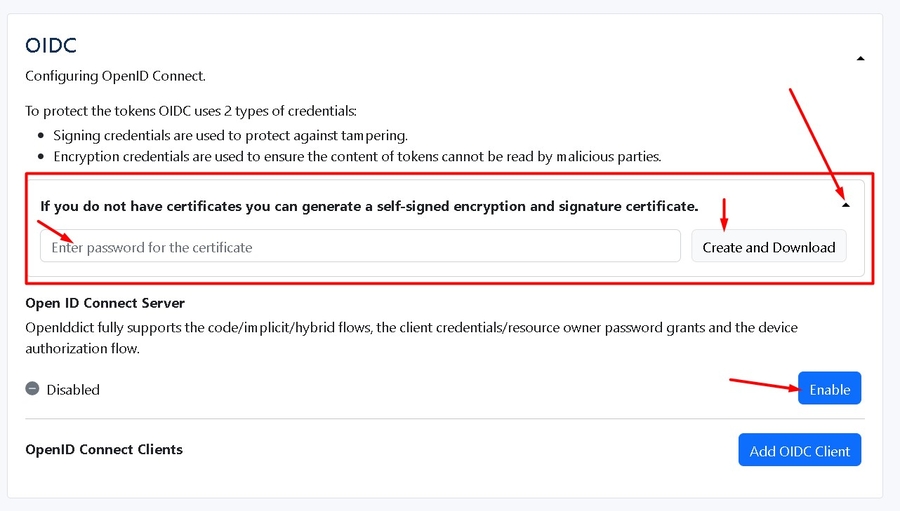
Download two types of Certificates, enter passwords, and click Next
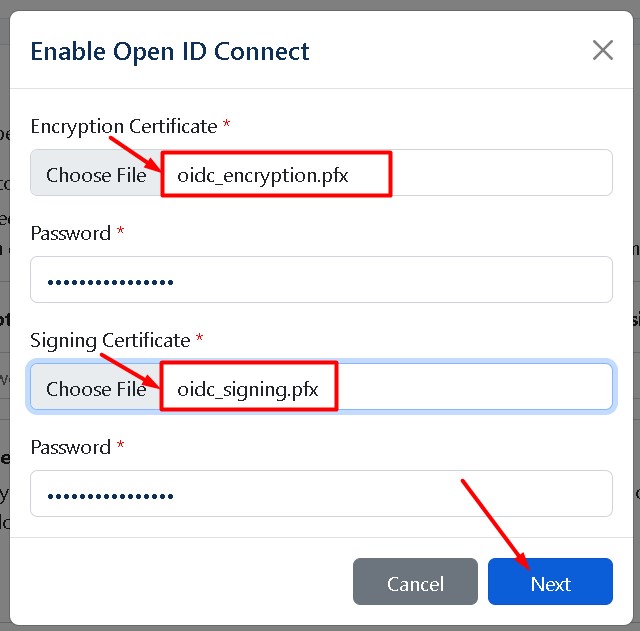
Restart your server
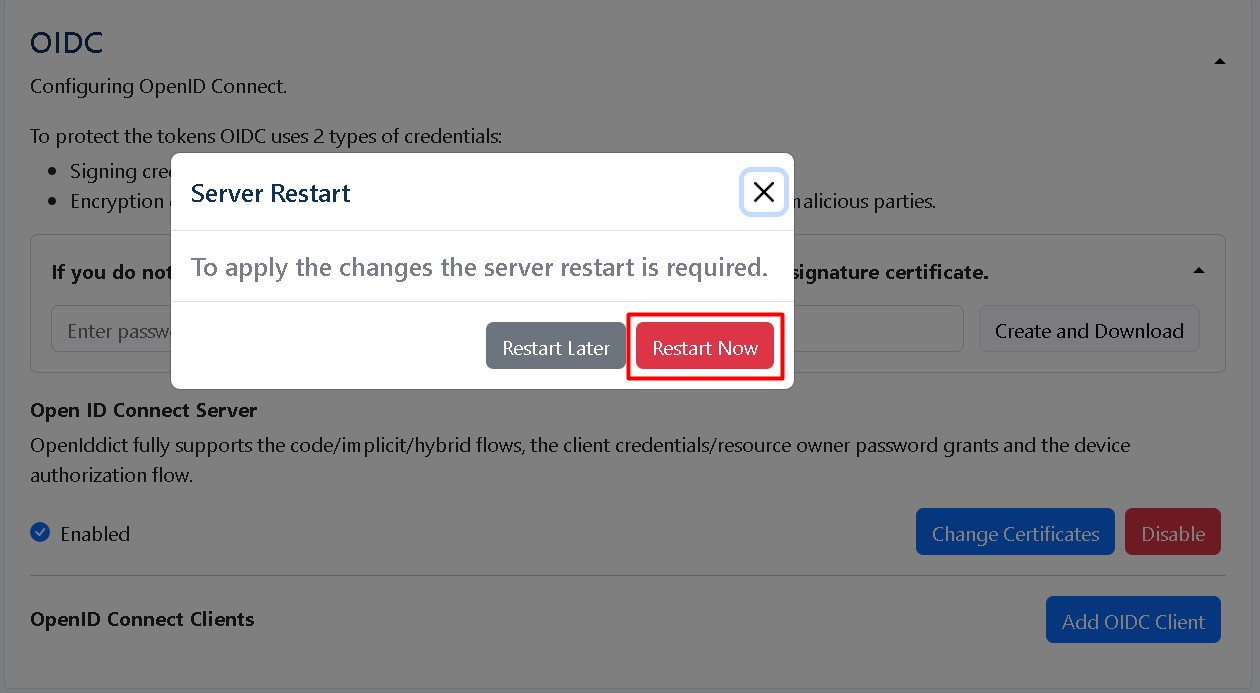
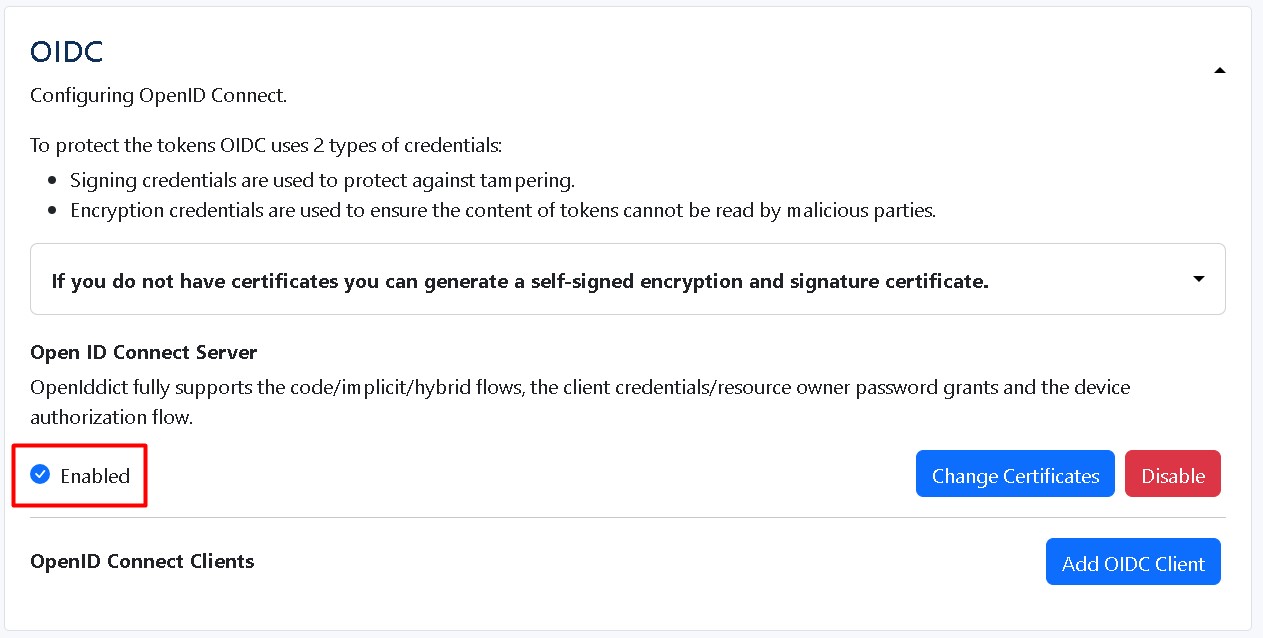
After restarting the HES server, OIDC will Enable
Add Openid connect client
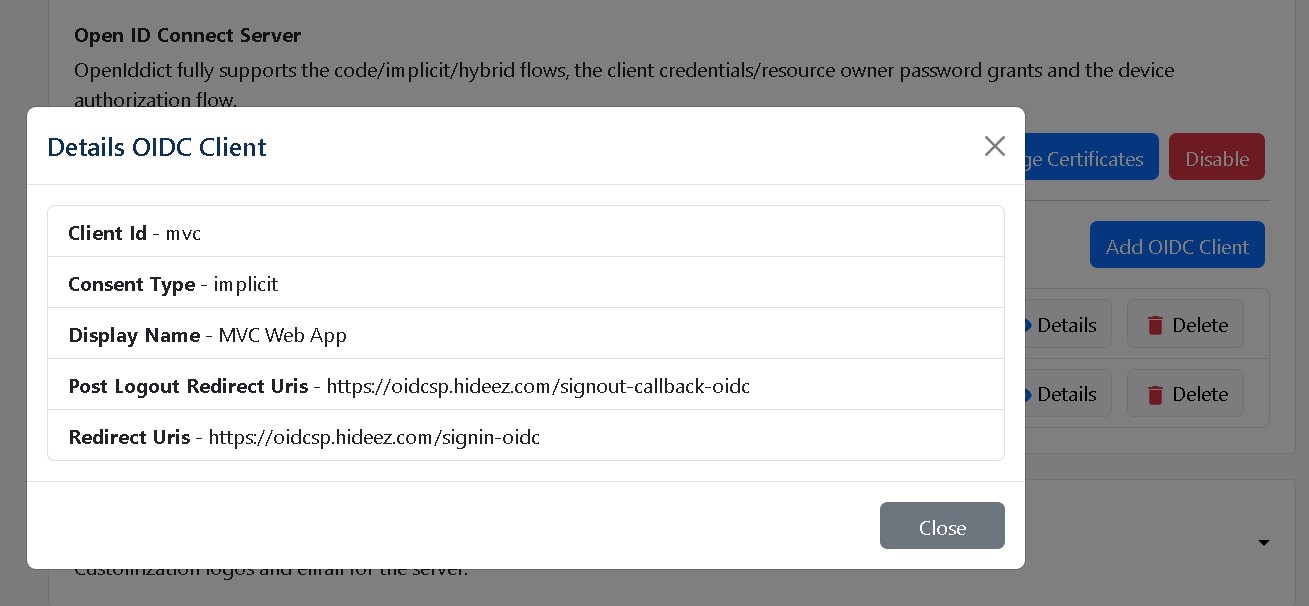
As you are the Administrator, you have to set Openid connect client:
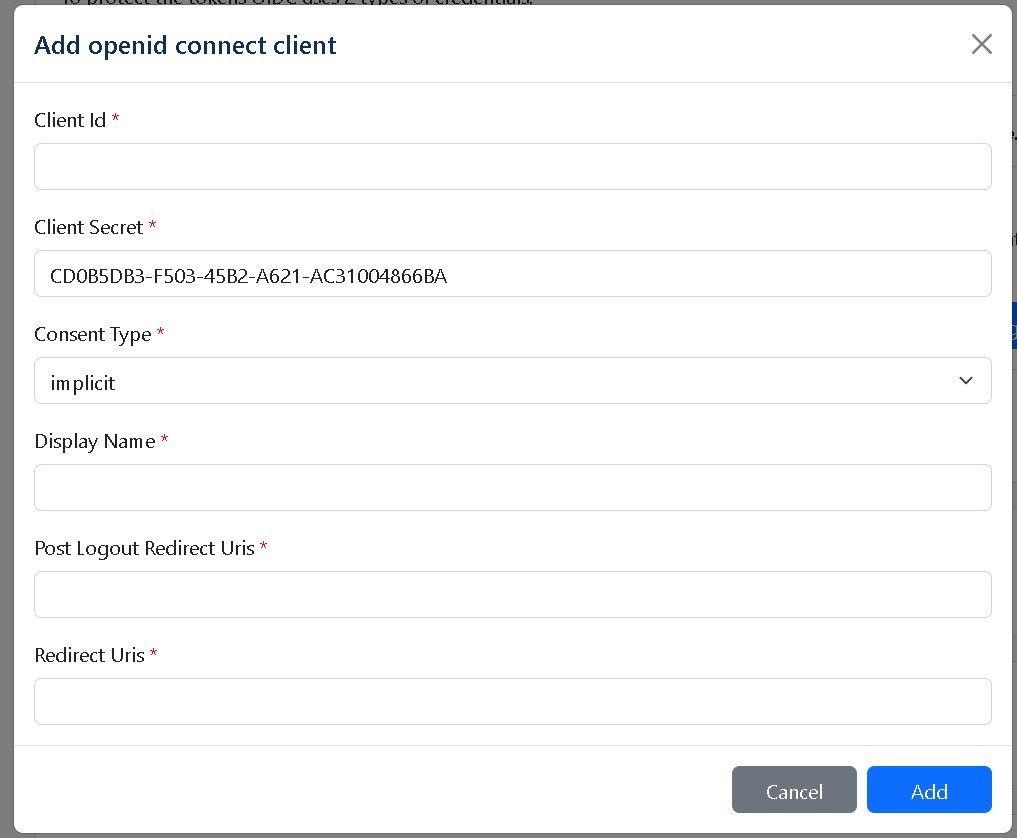
Please see, as an example configuration of our OpenID connect client:
Please see examples of services on how to integrate OIDC on Hideez Server.