Synchronization and import employees from Active Directory
Synchronization and import employees from Active Directory On-premises and Azure AD (Entra)
Last updated
Synchronization and import employees from Active Directory On-premises and Azure AD (Entra)
Last updated
Active Directory on-premises
These parameters must be specified if you will use HES scenarios for working with AD. Import and sync users from Active Directory Import and sync users from Active Directory with domain password changing
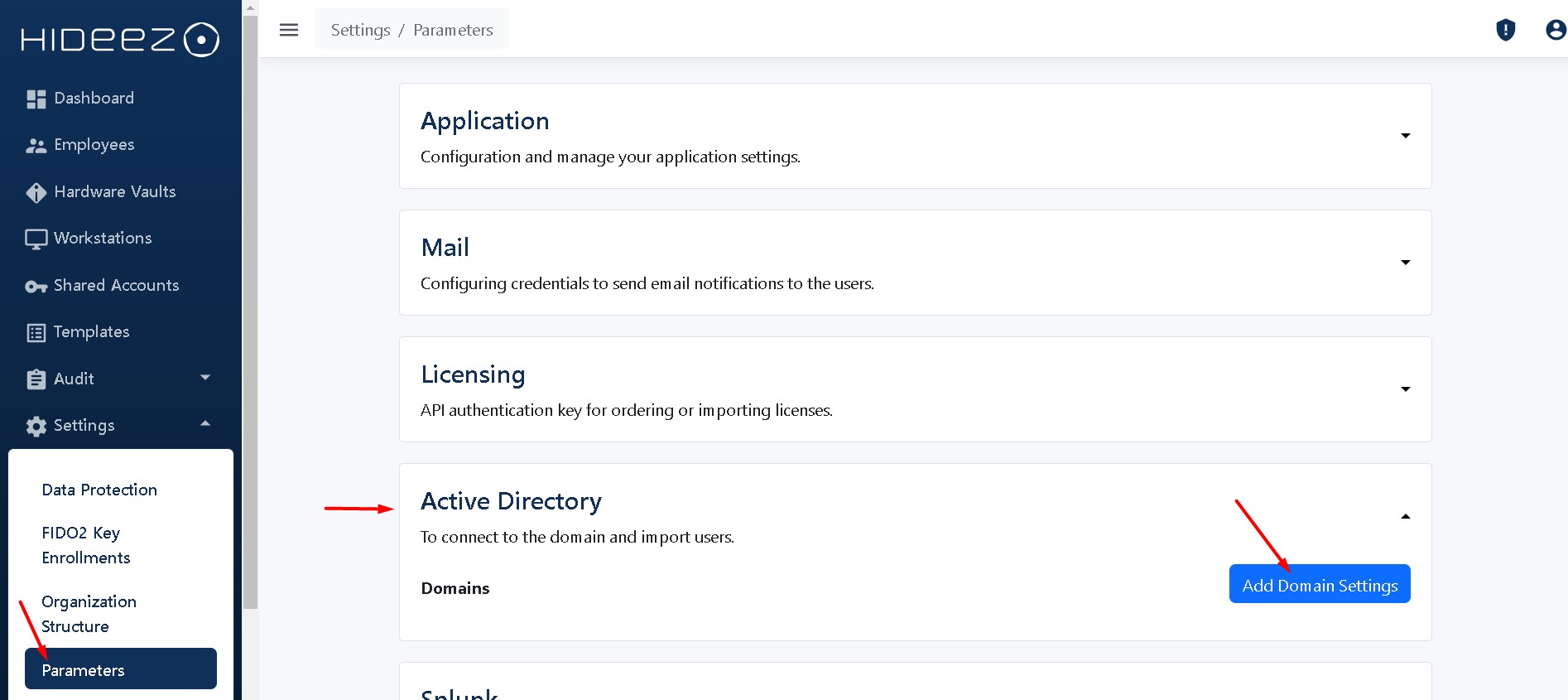
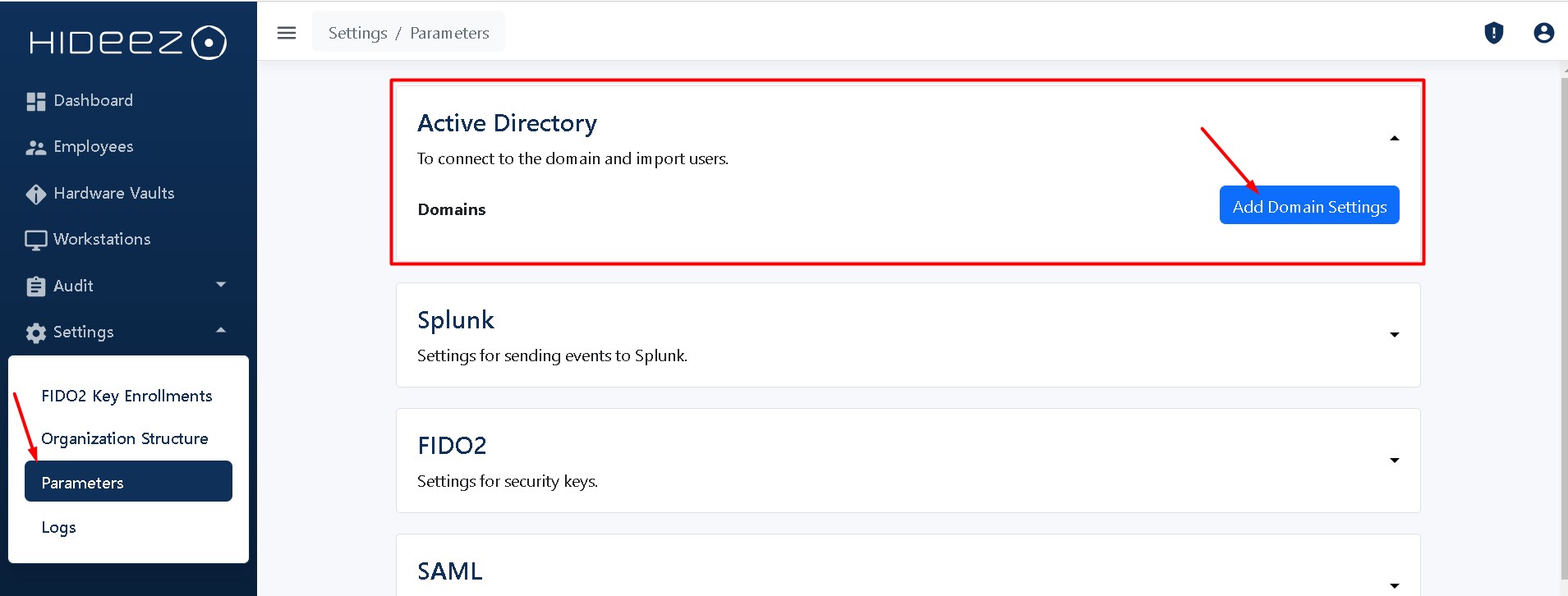
Click the button Settings→Parameters→Add Domain Settings
Active Directory Domain Name *: enter your Active Directory domain. This is necessary to import users from previously created groups in AD.
User Logon Name: AD administrator's login with permissions to get users and groups from the AD and change user passwords.
Password: AD administrator's password with permissions to get users and groups from the AD and change users' passwords.
Users Sync Group Name * - Users added to the sync group in the Active Directory will be automatically imported to the HES during synchronization. If the user is removed from group, he remains in the HES employees list. Synchronization with Active Directory is done once an hour.
Users Auto Password Change Group Name * - If the user is a member of both the sync group and auto password change group, then the domain account will be imported during synchronization, and a new password will be generated. When the new password is written into the Hideez Key simultaneously, it will be changed in the Active Directory. From this time, the user has to use his Security Key to login. Further scheduled password changes will follow the same algorithm. If the user is removed from the auto password change group, the automatic password change logic stops working.
You can set any default group names, but these names must match the groups in your On-Premises Active Directory for user synchronization or automatic password changes.
Auto Password Change (days): number of days after which it is necessary to change the password from the domain account to users from the Security Key Auto Password Change group.
1. Connecting to AD to Retrieve the User List
Any AD user can retrieve the list of other users.
If password changes are not required, connect to AD using an account with minimal privileges.
2. Changing Passwords, Locking, and Unlocking AD Users
These actions can only be performed by:
AD Administrators.
Members of the Account Operators or Domain Admins group.
Users with delegated rights to change passwords. ()
To connect to AD from the HES side, use an account with the appropriate permissions.
3. Delegating Rights to Change Passwords
To delegate rights to another user or group, follow these steps (administrator rights are required):
Launch the Active Directory Users and Computers (ADUC) Console:
Right-click on the OU containing the users.
Select Delegate Control from the menu.
Select the User or Group for Delegation:
Choose the user or group that needs the right to change passwords or other additional permissions:
Granting Rights:
Mark the necessary rights for delegation:
Create, delete, and manage user accounts
Reset user passwords and force password change at next logon
Important Note:
If you delegate rights to a regular user, to change passwords, they will be able to change passwords for all regular users except administrators.
To connect the Azure AD with the HES, please, first, set the Azure AD application:
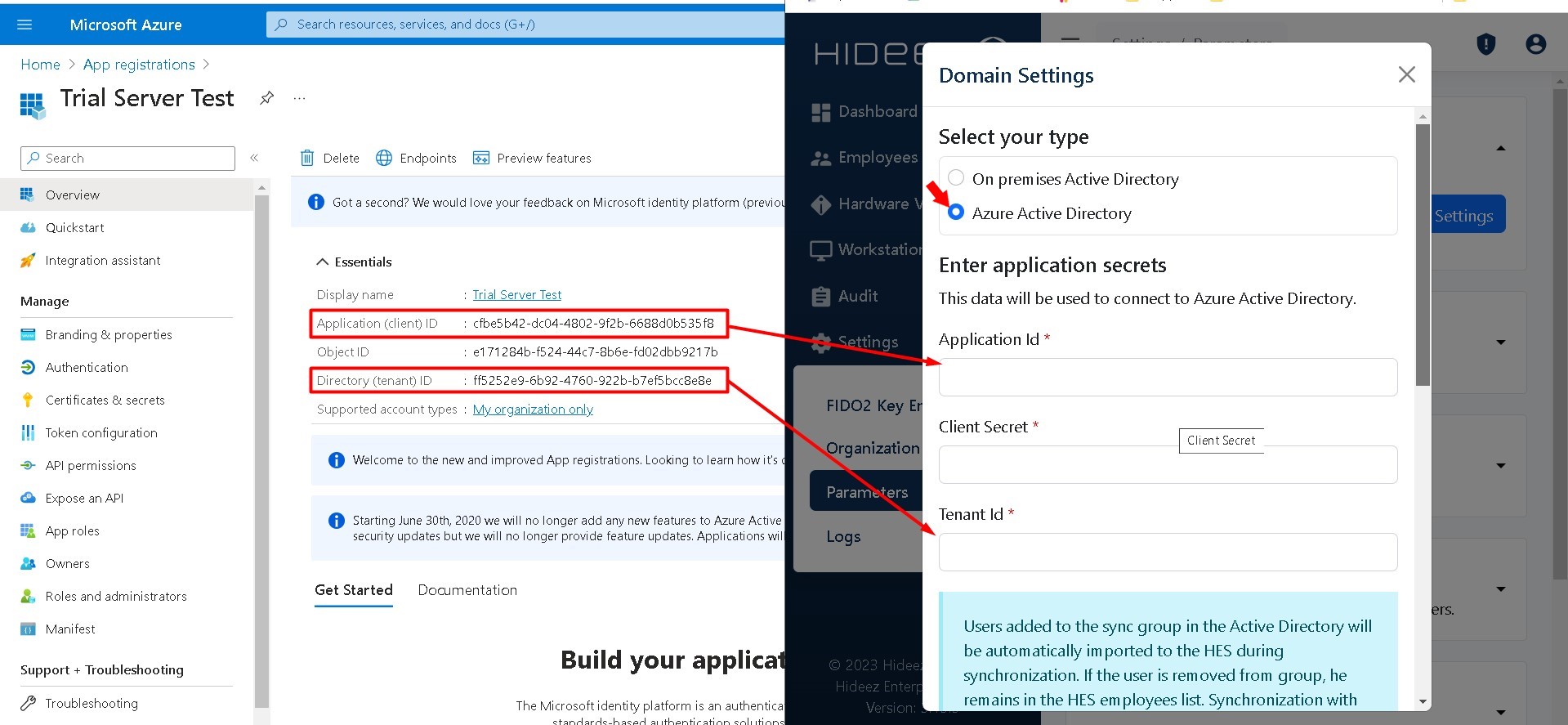
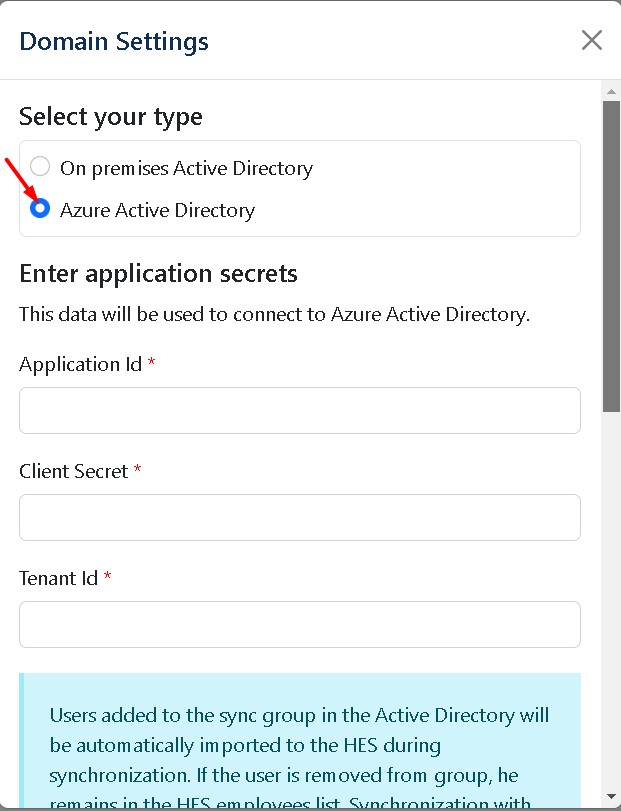
Open Settings→Parameters→Add Domain Settings→ select radio button Azure Active Directory
Login to the Azure portal
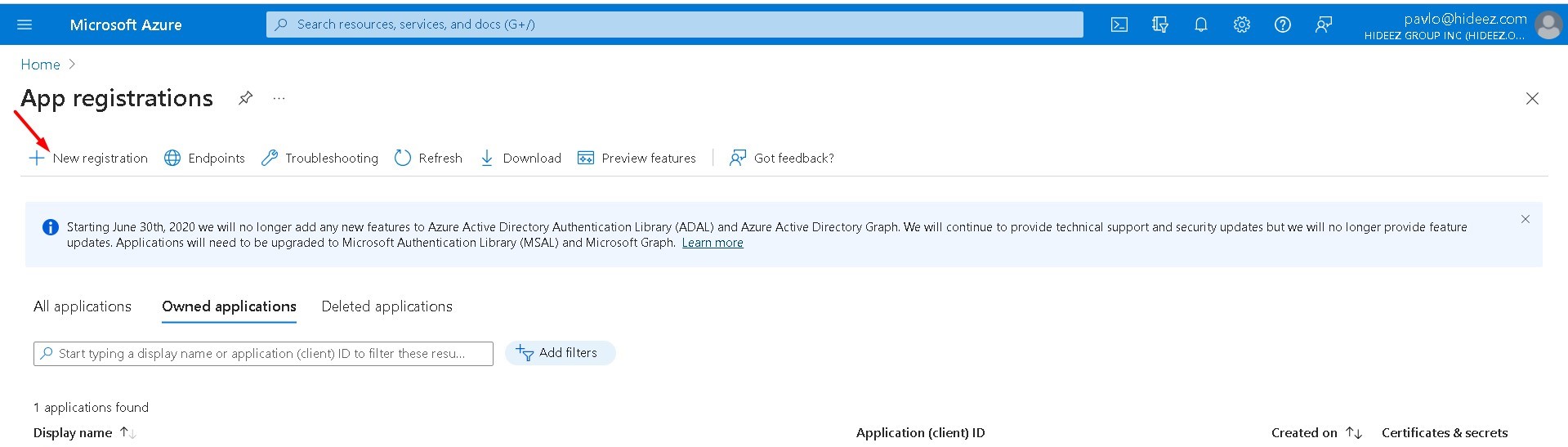
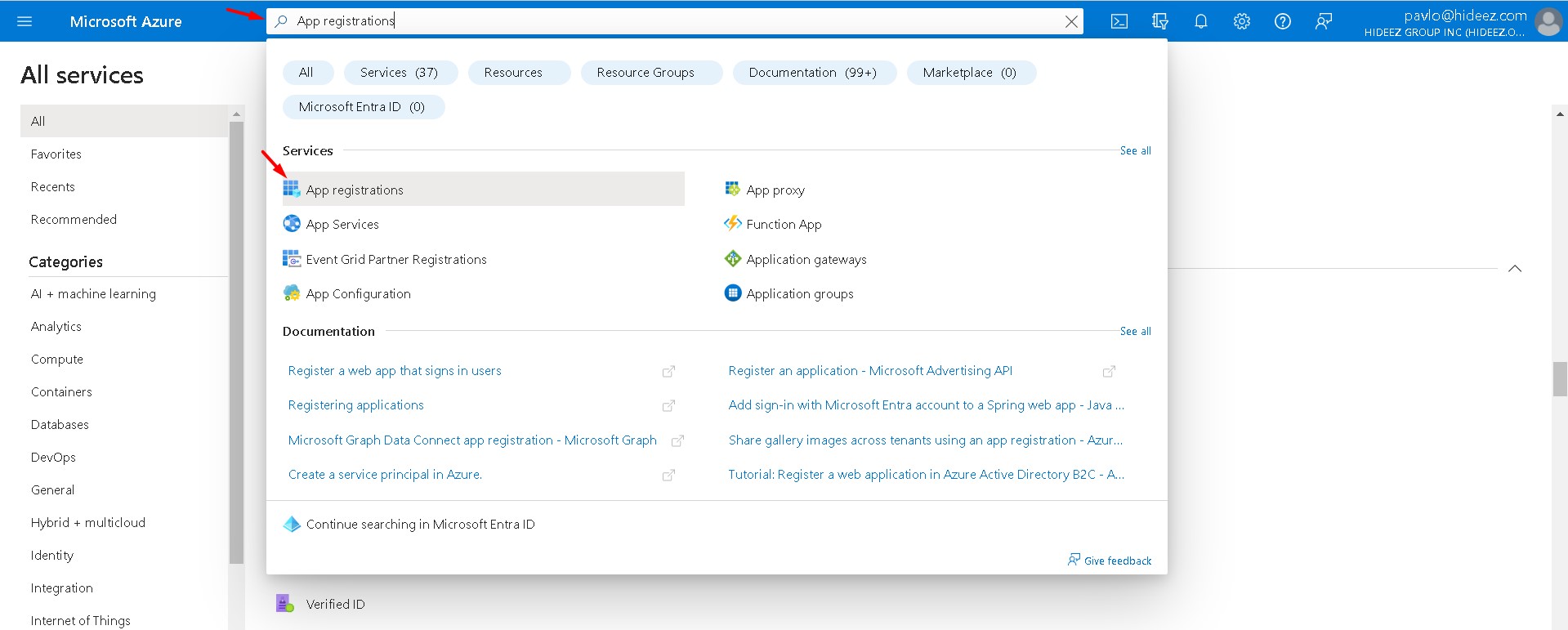
Go to the Azure Active Directory → App registrations
Click New Registration
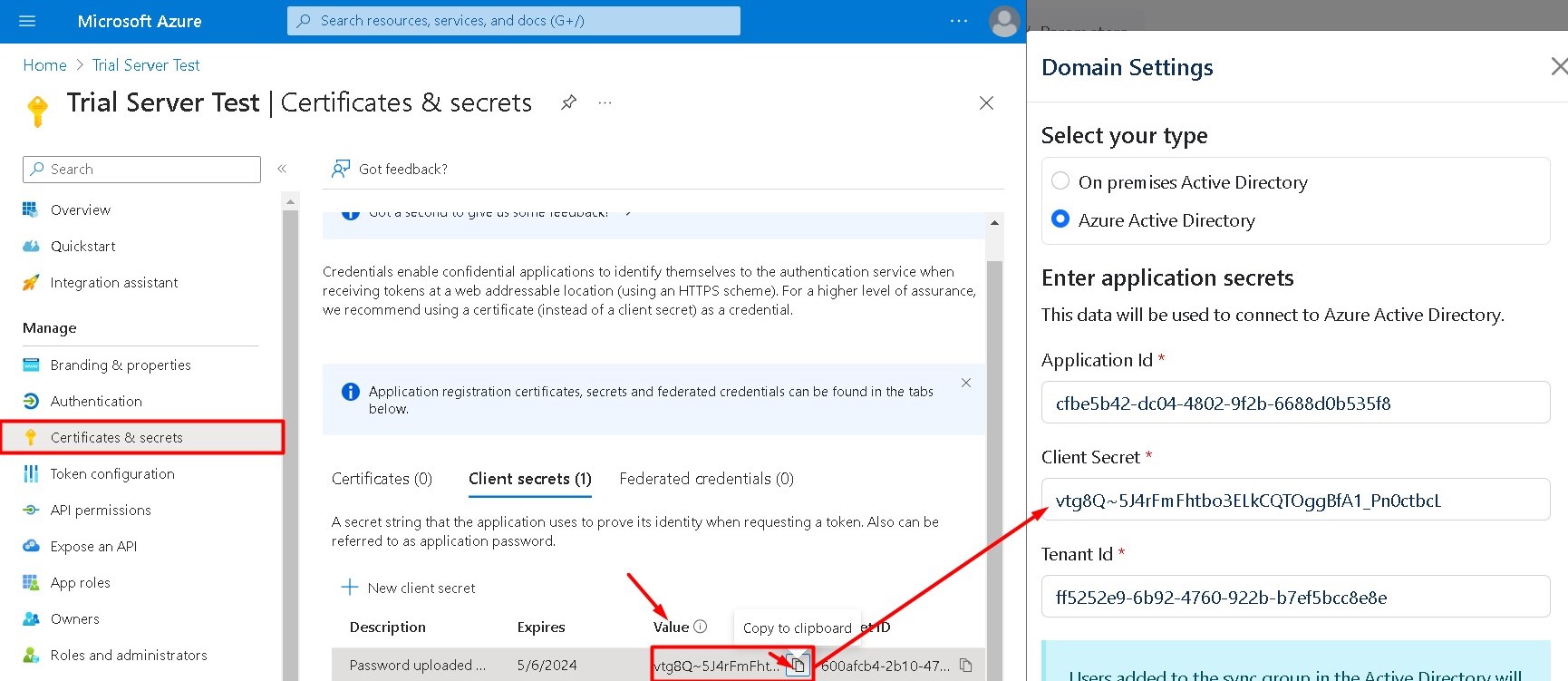
Go to app overview copy the Application (client) ID, and Directory (tenant) ID, and paste those values into Domain Settings on Hideez Server
Application ID: enter your Azure AD application id.
Client secret: enter your Azure AD client secret.
Tenant ID: enter your Azure AD tenant id.
Auto Password Change (days): number of days after which it is necessary to change the password from the domain account to users from the Security Key Auto Password Change group.
After saving the data, login parameters are not displayed in the setting
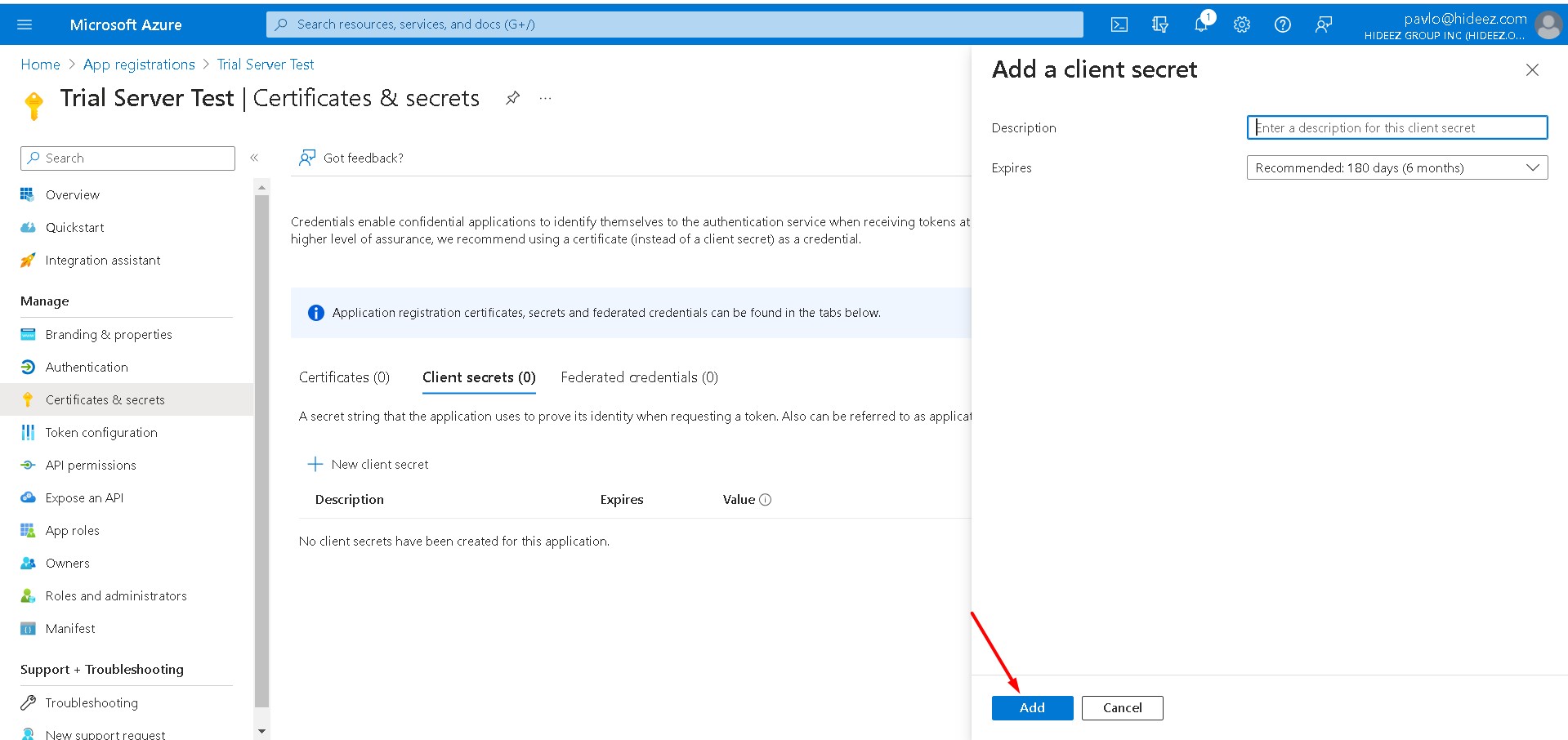
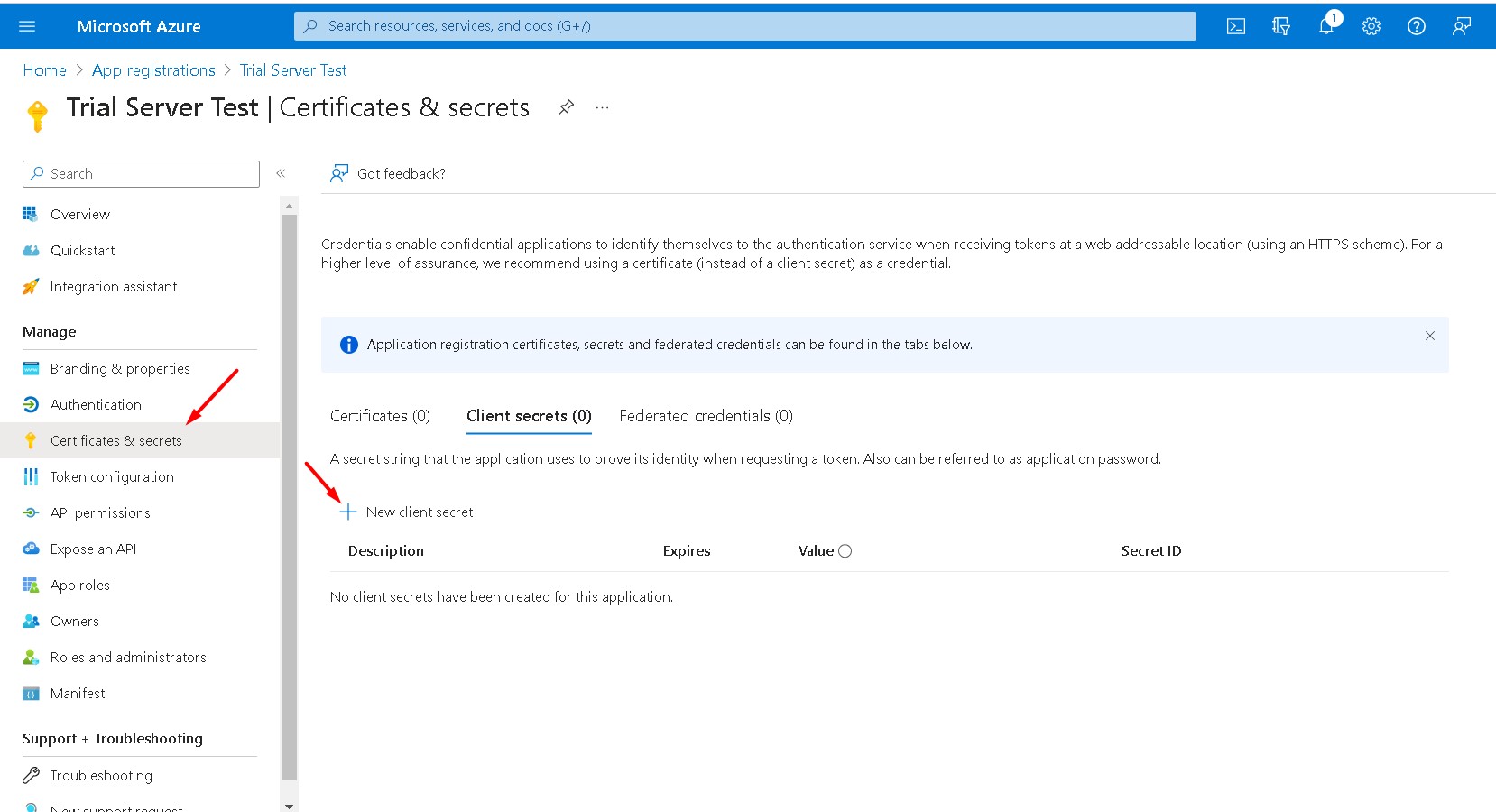
On Azure portal, go to the Certificates & secrets → New client secret and then add and copy Client Secret
Copy the secret from column Value and paste it to the field Client Secret on Hideez Server
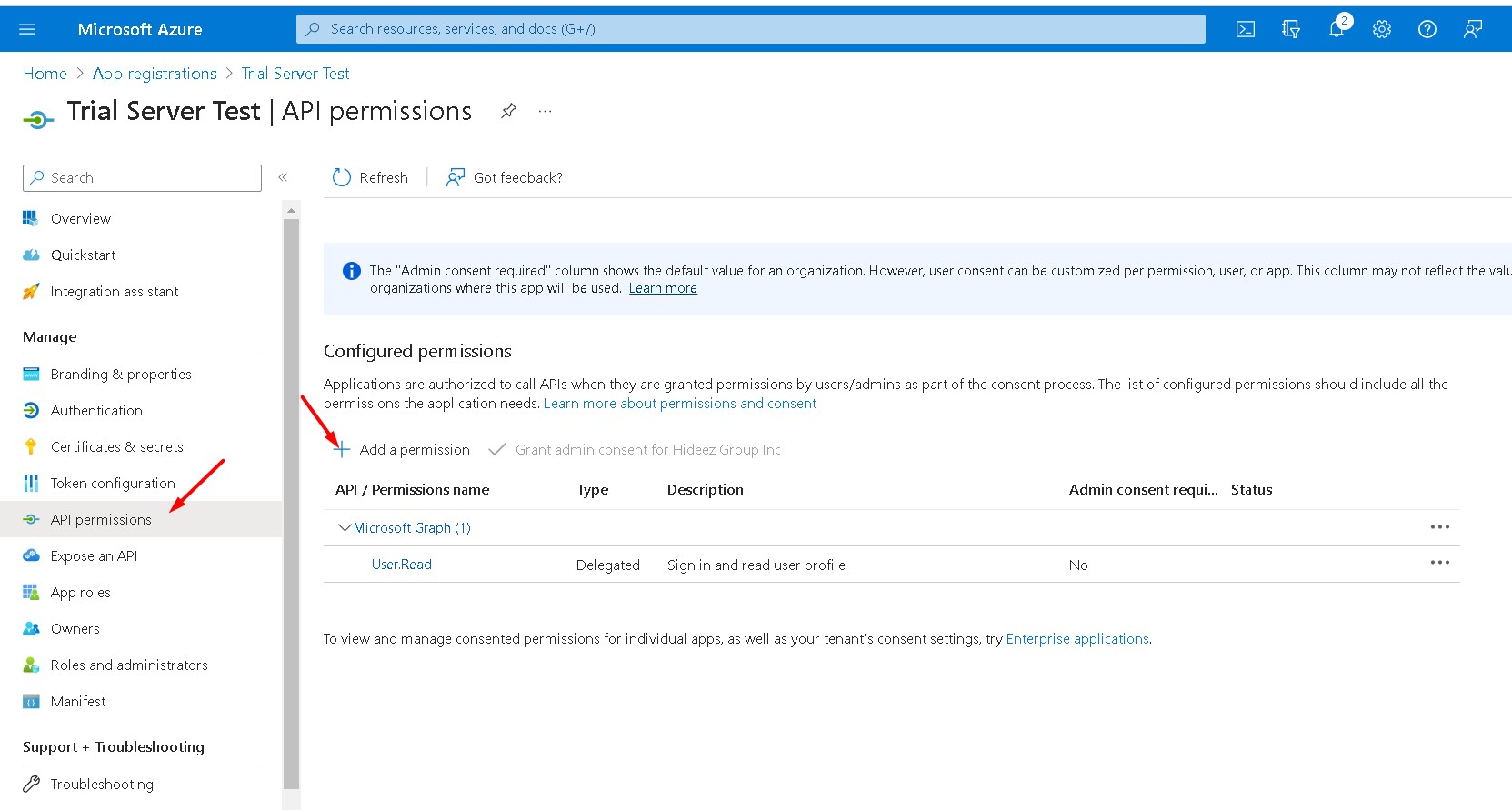
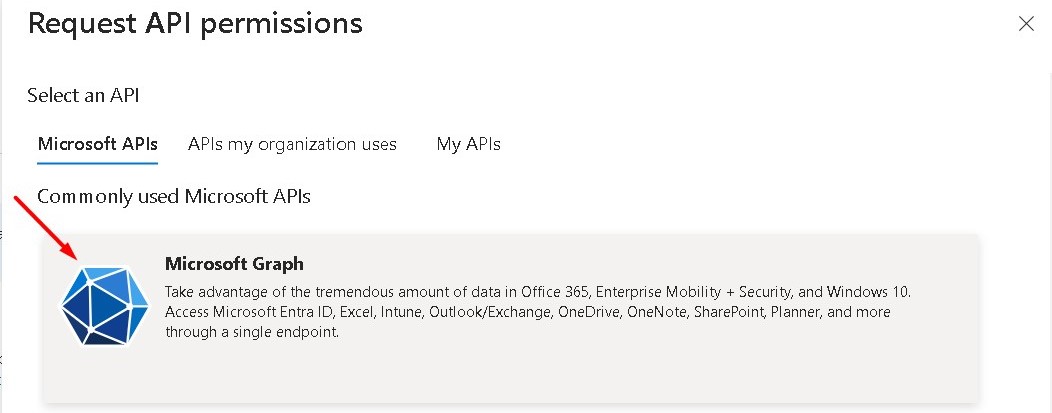
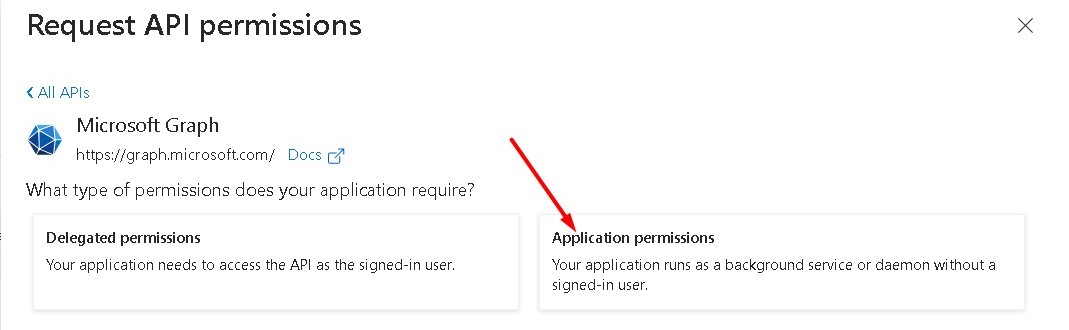
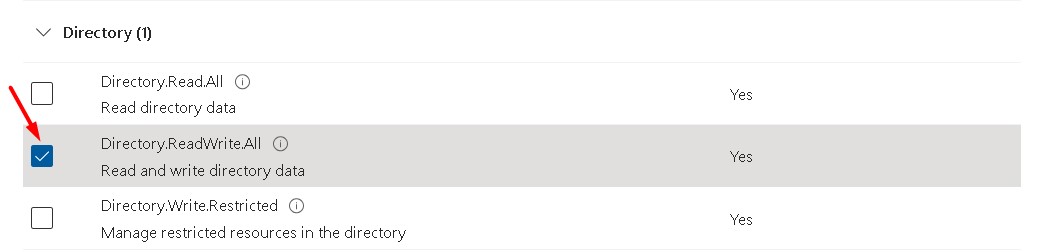
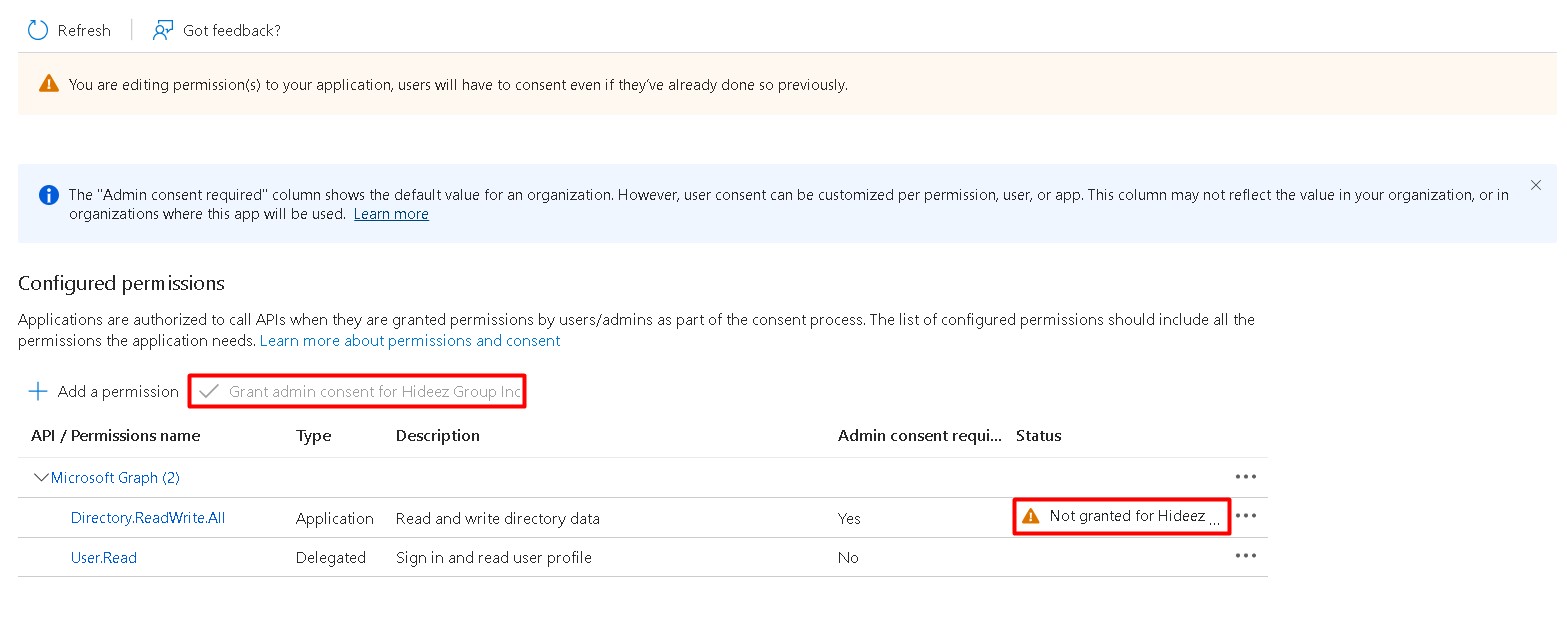
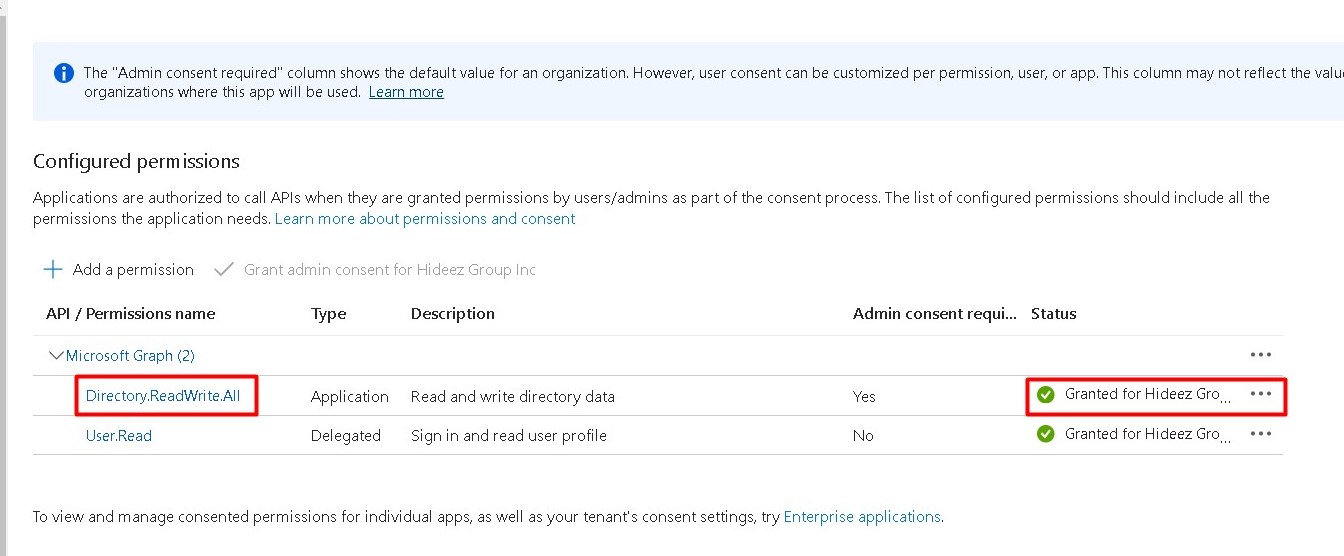
On Azure portal, go to the API permissions -> Add a permission -> Microsoft Graph
Click Grant admin consent
Application ID: enter your Azure AD application id.
Client secret: enter your Azure AD client secret.
Tenant ID: enter your Azure AD tenant id.
Auto Password Change (days): number of days after which it is necessary to change the password from the domain account to users from the Security Key Auto Password Change group.
After saving the data, login parameters are not displayed in the settings.
If you use Linux and need the AD integration, join your Linux server to the AD
Be aware! As soon as you remove the AD administrator login and password from the settings, all AD sync scenarios will stop working.
With this instruction, you can add on server several domains at the same time. Each domain is managed separately.
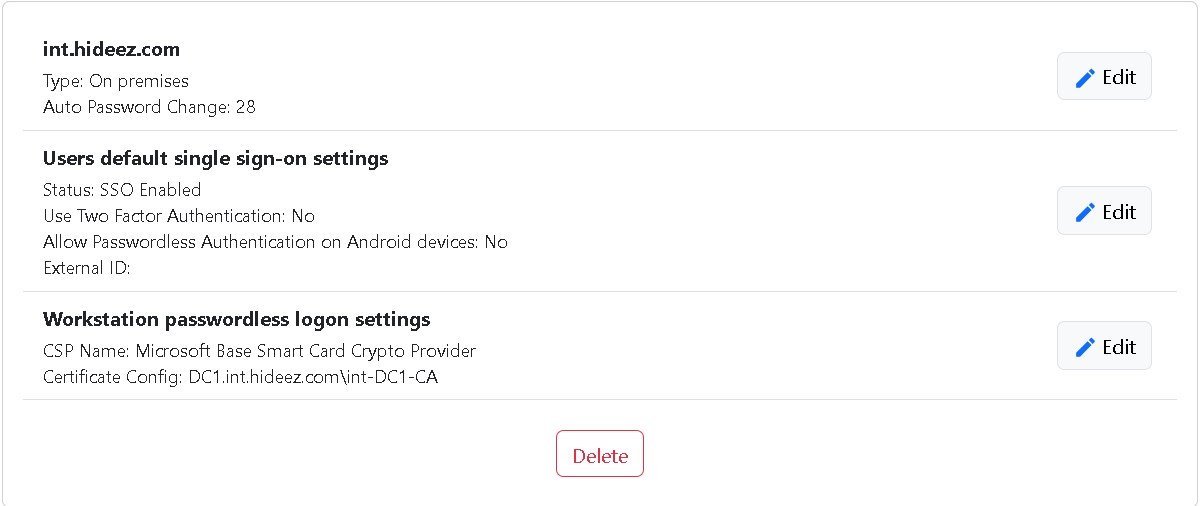
Domain Settings – These credentials will be used to connect to Active Directory via LDAPS
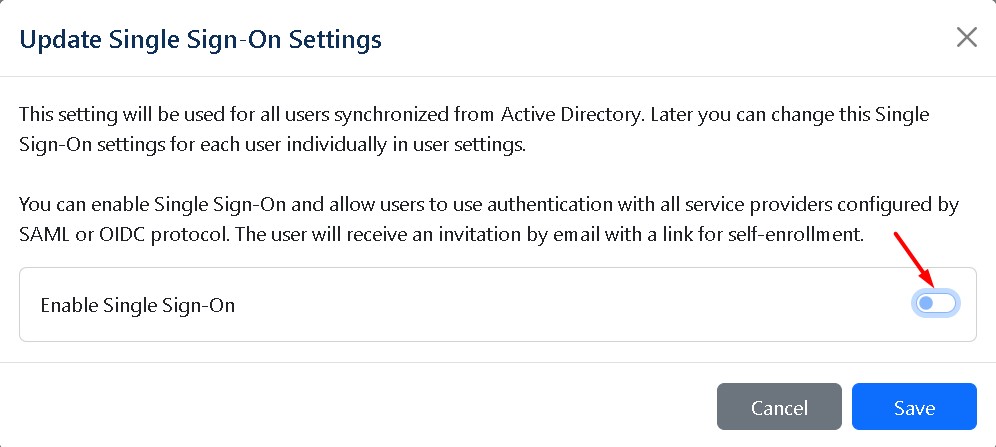
Users default single sign-on settings - This setting will be used for all users synchronized from Active Directory. Later you can change this Single Sign-On setting for each user individually in user settings.
Workstation passwordless logon settings - Update Workstation Passwordless Logon Settings.