Configuring an Active Directory Certification Authority
How does passwordless authentication work?
It is based on Microsoft Virtual Smart Card technology - which allows you to log in to domain accounts using smart cards, not physical but virtual. As with regular smart cards, this is possible if you set up a domain controller and certification authority. A virtual smart card is created on a workstation using the TPM module.
When initializing a virtual smart card, part of the information required to log in to the account (smart card credentials) is transferred to the mobile application and stored there. During the logon, the user scans the QR code on the computer screen, which allows you to establish a connection between the computer and the phone, after which the smart card credentials are transferred to the computer and then PC is unlocked.
Active Directory Certification Authority setup
On Certification Authority, you need to create a template for the certificate that you will request for the virtual smart card.
To create the certificate template:
On your server, open the Microsoft Management Console (MMC). One way to do this is to type mmc.exe from the Start menu, right-click mmc.exe, and click Run as administrator.
Click File, and then click Add/Remove Snap-in.

In the available snap-ins list, click Certificate Templates, and then click Add.

Certificate Templates is now located under Console Root in the MMC. Double-click it to view all the available certificate templates.
Right-click the Smartcard Logon template, and click Duplicate Template.

On the Compatibility tab, under Certification Authority, review the selection, and change it if needed.

On the General tab:
Specify a name, such as TPM Virtual Smart Card Logon.
Set the validity period to the desired value.
On the Request Handling tab:
Set the Purpose to Signature and smartcard logon.
Click Prompt the user during enrollment.
On the Cryptography tab:
Set the minimum key size to 2048.
Click Requests must use one of the following providers, and then select Microsoft Base Smart Card Crypto Provider.
On the Security tab, add the security group that you want to give Enroll access to. For example, if you want to give access to all users, select the Authenticated users group, and then select Enroll permissions for them.
Click OK to finalize your changes and create the new template. Your new template should now appear in the list of Certificate Templates.
Select File, then click Add/Remove Snap-in to add the Certification Authority snap-in to your MMC console. When asked which computer you want to manage, select the computer on which the CA is located, probably Local Computer.

In the left pane of the MMC, expand Certification Authority (Local), and then expand your CA within the Certification Authority list.
Right-click Certificate Templates, click New, and then click Certificate Template to Issue.

From the list, select the new template that you just created (TPM Virtual Smart Card Logon), and then click OK. Note: It can take some time for your template to replicate to all servers and become available in this list.

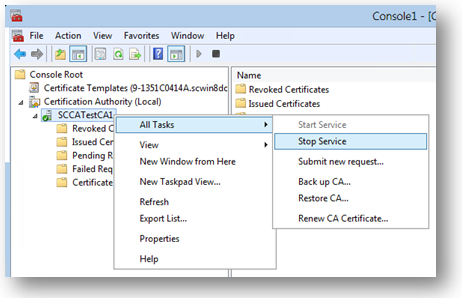
After the template replicates, in the MMC, right-click in the Certification Authority list, click All Tasks, and then click Stop Service. Then, right-click the name of the CA again, click All Tasks, and then click Start Service.