Configuring SAML Protocol
Hideez Enterprise Server – SAML Protocol
Hideez Enterprise Server supports SAML 2.0 (Security Assertion Markup Language) for secure user authentication, acting as an Identity Provider (IdP) for single sign-on (SSO) across web applications (Service Providers, SP) that support SAML 2.0. By setting up Hideez Server as an IdP, organizations can simplify login processes for users across integrated web applications.
Key Features
With Hideez Server’s support for FIDO2 passwordless authorization, service providers gain the ability to authenticate users through:
Hardware security keys (e.g., YubiKey)
Passkeys
Hideez Authenticator App
Supported Sign-in Options
Username + password (not recommended)
Username + password + second factor (security key: hardware or platform, OTP, mobile authenticator)
Passwordless, User nameless (without typing login and password)
To set up Hideez Server as an IdP, follow these steps:
When a user logs into an application through SAML, the Hideez ( as an IdP) transmits a SAML assertion to the user's browser, which is then forwarded to the Web application (as an SP). Then Hideez Server authenticates the user.
Since Hideez Server supports FIDO2 passwordless authorization, service providers automatically get the ability to authorize with hardware security keys without having to create and enter passwords.
Thanks to Hideez Server's support for FIDO2 passwordless authorization, Service Providers (web applications) gain the ability to authorize users using hardware security keys, Passkey, and Hideez Authenticator App, eliminating the need to create or enter passwords.
Supported sign-in options:
Username + password (not recommended)
Username + password + second factor (security key: hardware or platform, OTP, mobile authenticator)
Passwordless, Usernameless (without typing login and password)
Configuring Hideez Server as an Identity Provider (IdP)
Hideez Server (IdP) and Service Providers (SP, i.e., web applications) must exchange public key certificates or metadata.
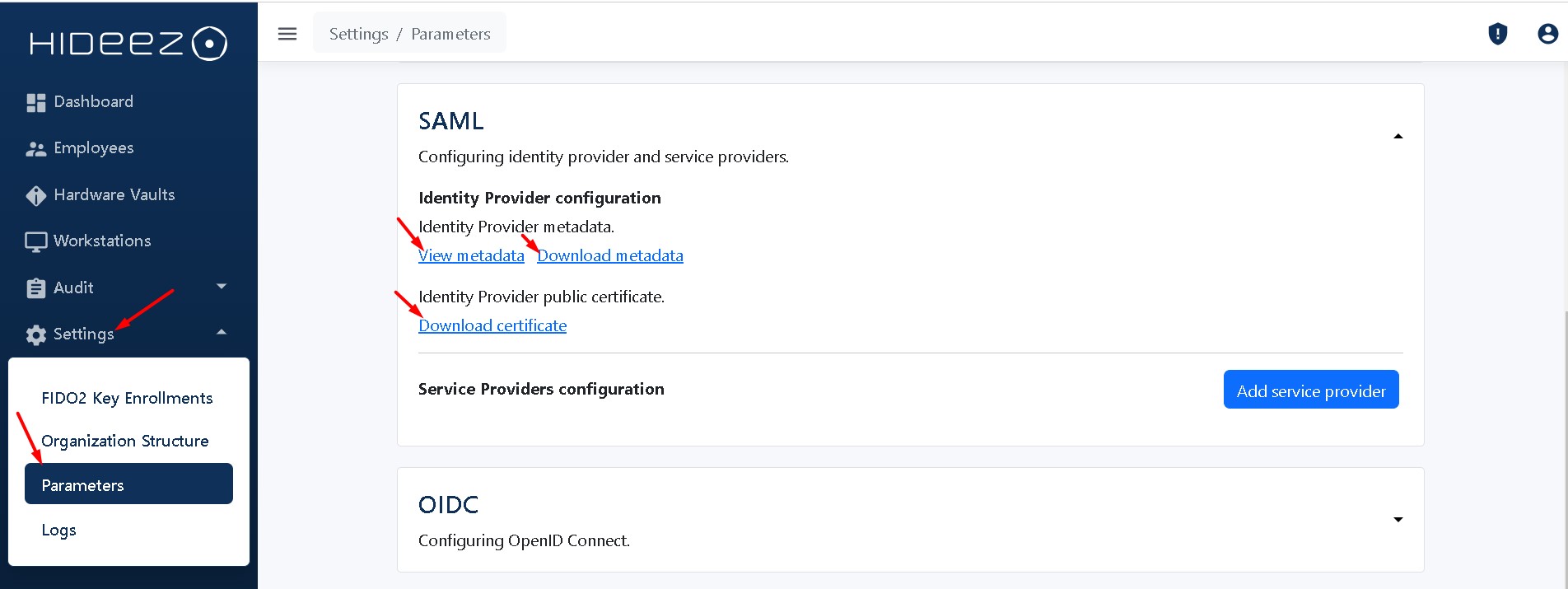
Go to Parameters →Settings → SAML.
Here you can get the necessary data that you have to provide your Service Provider:
Download metadata
View metadata
Download certificate
Adding SP (Service Provider)
Click Add Service Provider

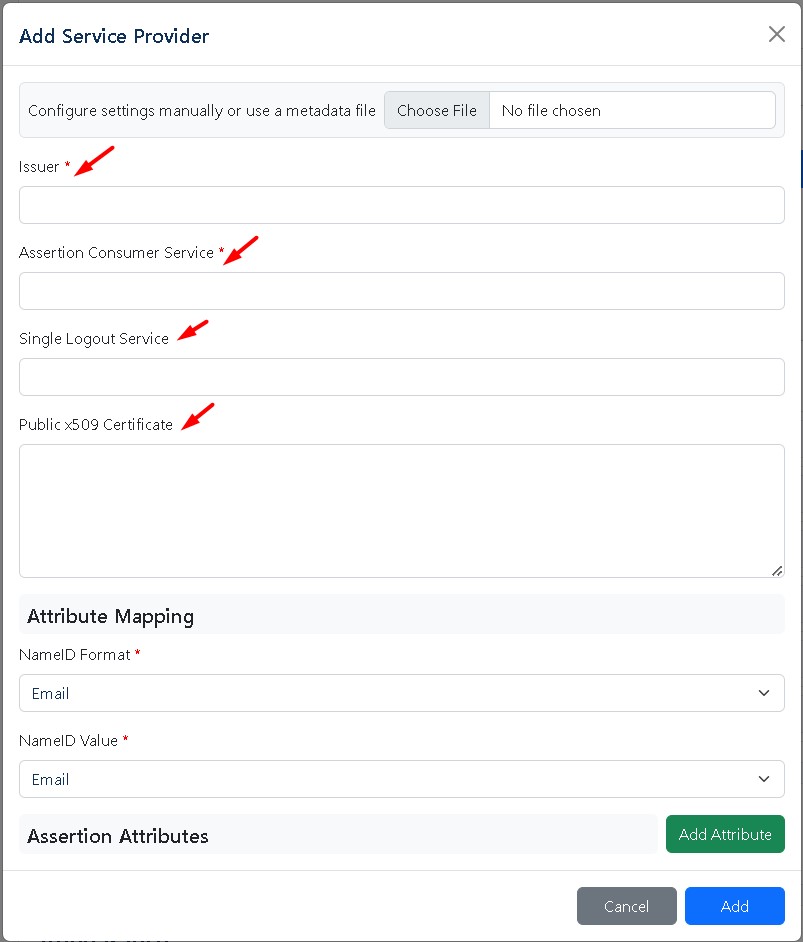
In the opened tab file, the corresponding fields:
Issuer - a random unique SP name you need to copy from the SP settings or extract from the metadata file.
Assertion Consumer Service – the login address on the side of the service provider. Redirection is done to this address following the successful login through the Hideez Server. Single Logout Service – the address to log out of the account. If you exit Hideez Server, this URL is opened in the loop for all web applications. Public x509 Certificate – the public key certificate of the service provider.
Some Service Providers provide users with metadata files. In this case, all required fields will be filled in automatically after importing the metadata file.
Otherwise, you can configure settings manually. In this case, the settings depend on the specific Service Provider.
You can download metadata files from your computer:
Attribute Mapping
When a user authenticates through SAML, Hideez Server generates a SAML assertion that contains information about the user (such as their name, email, roles, etc.). Attribute Mapping specifies how these attributes are matched and passed from the Hideez Server (IdP) to the SP, and how they are subsequently used by the SP for authorization and access control.
Assertion Attributes.
These attributes are provided by the Hideez Server (IdP) in a SAML assertion to the Service Provider (SP) during the authentication process. The Service Provider uses these attributes to make authorization decisions and personalize the user's experience within the application.
Attribute names and formats are typically defined and agreed upon by Hideez Server (IdP)and SP during the configuration of the SAML integration. This allows for seamless information exchange between the two entities.
Attribute Mapping and Assertion Attributes could be configured automatically after downloading the metadata file.
After filling in and saving all the settings, you can check the integration by logging into the service provider. You should be redirected to the HES authentication page, where you will need to enter your username (email) and pass the security key verification.
Please, see some use cases for how to configure Hideez as IdP on web services:
Here's a list of web applications (SP) where Hideez Server can be implemented as an Identity Provider (IdP):
Please see examples of services on how to integrate SAML 2.0 on Hideez Server.
While the list provided is not exhaustive, each web service may have its own specific configuration. If you require assistance in integrating your web app with Hideez Server using SAML, don't hesitate to contact us. We're here to help.
Last updated